Auditing User Permissions in IAM
An audit gives you an opportunity to remove unneeded IAM users, roles, groups, and policies, and to make sure that your users and software have only the permissions that are required. Periodically audit your security configuration to make sure it meets your current business needs.
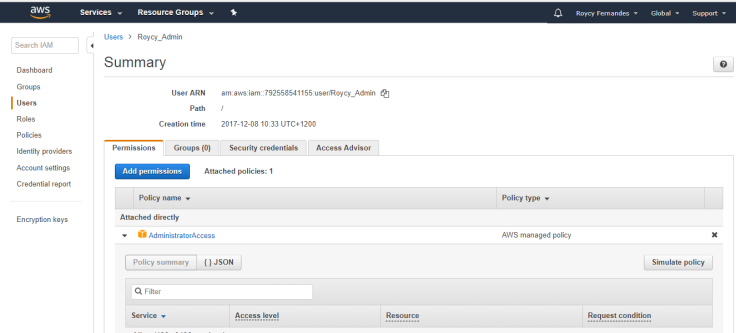
Use the IAM Policy Simulator to test policies that are attached to users or groups.
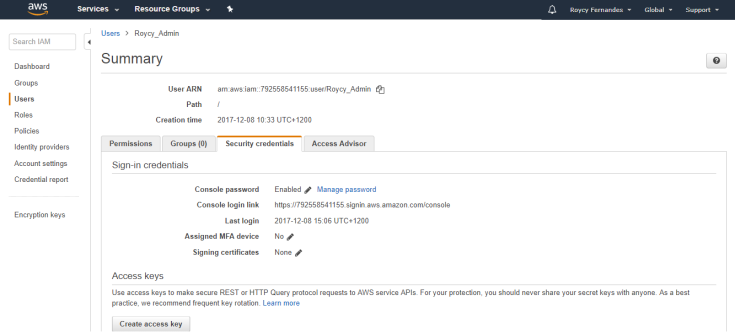
Remove root access keys for your account if you dont use them. AWS recommends that you do not use root access keys for everyday work, and that instead you create IAM users.
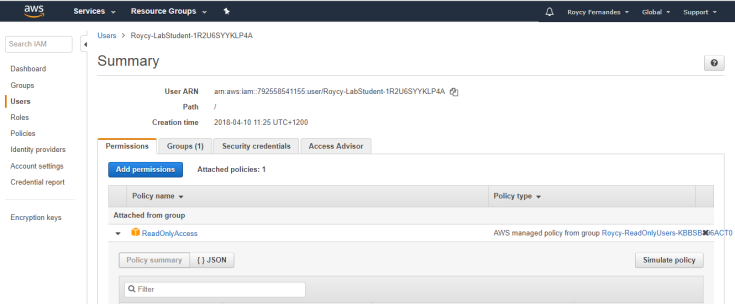
Make sure policies don’t grant permissions for services that you don’t use.
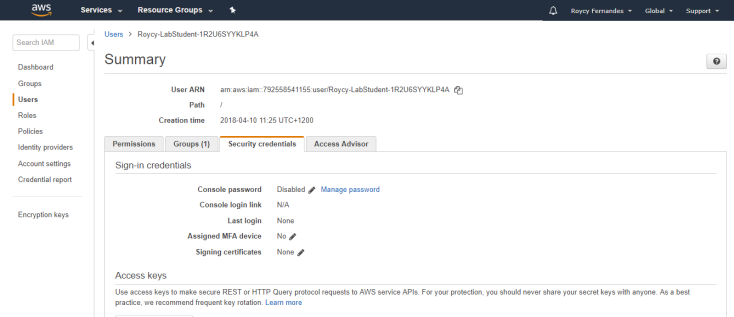
The user security credentials periodically, or immediately if you ever share them with an unauthorized person.
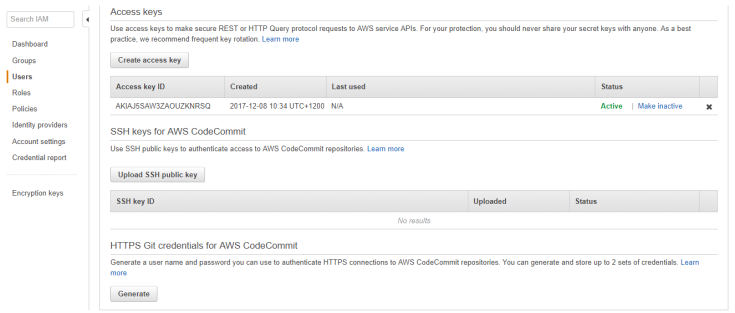
Review the access policy for the role to be sure that it grants suitable permissions to whoever assumes the role.
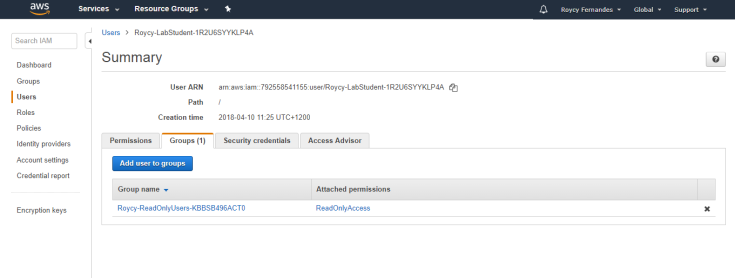
Attach policies to groups instead of to individual users.
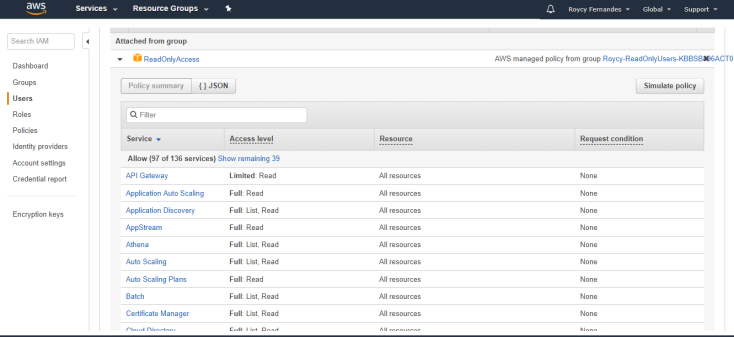
Ensure that IAM users, groups, and roles have only the permissions that they need.
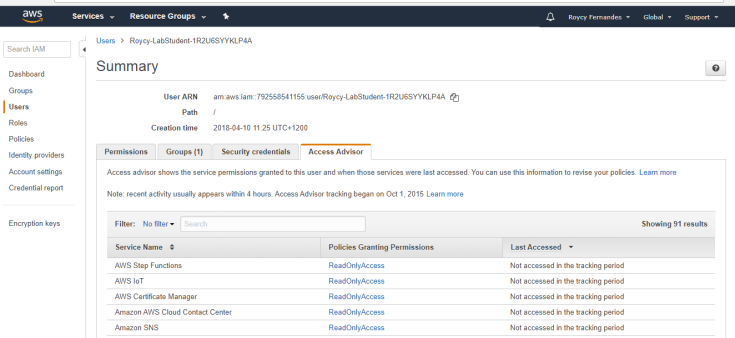
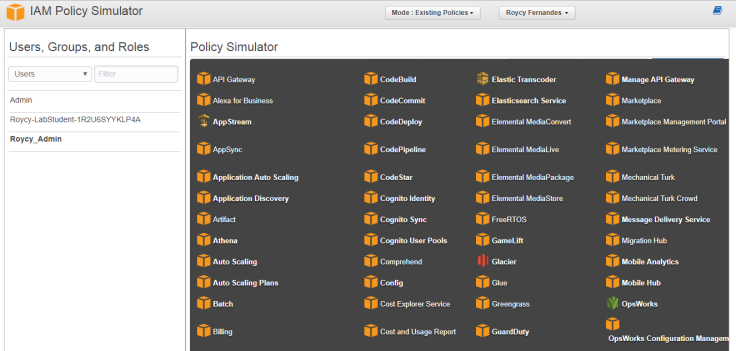
Run IAM Policy Simulator
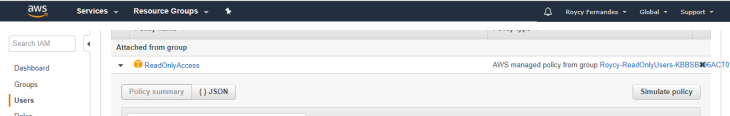
With the IAM policy simulator, you can test and troubleshoot IAM and resource-based policies. Test policies that are attached to IAM users, groups, or roles in your AWS account.
Thank You! 🙂

Leave a comment