Set up a firewall policy By default, the firewall blocks all non-essential connections. Therefore you must configure the firewall before you protect your computers. 1. In the Policies pane, right-click Firewall, and click Create Policy. A New Policy is added to the list, with its name highlighted. Type the name that you want to use... Continue Reading →
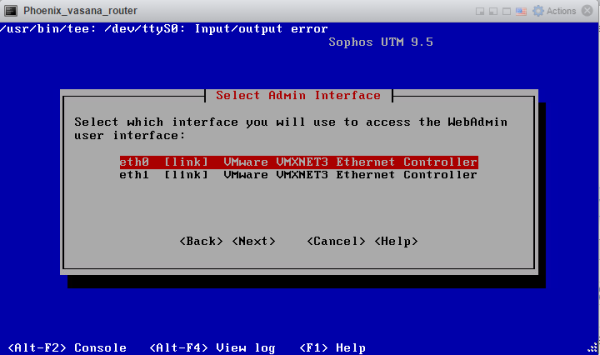
Sophos Router Installation
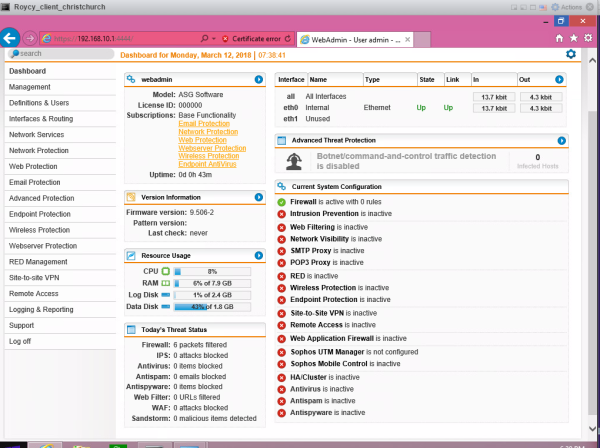
Sophos UTM 9.4 is one of the first Sophos products to offer our advanced next-gen cloud sandboxing technology. Sophos UTM is easy to use, thanks to the configurable real-time dashboard, flexible modular licensing, and intuitive reusable network object definitions. Installing Sophos helps to: ■ Create computer groups. ■ Set up security policies. ■ Search for... Continue Reading →
Basic Audit of AWS Environment – Cloud Watch
Auditing Cloud Watch Metrics and Alarms Amazon CloudWatch is a monitoring service for AWS cloud resources and the applications you run on AWS. You can use Amazon CloudWatch to collect and track metrics, collect and monitor log files, set alarms, and automatically react to changes in your AWS resources. Amazon CloudWatch can monitor AWS resources... Continue Reading →
Basic Audit of AWS Environment – VPC
Review Amazon VPC Security Configuration Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS. Security groups... Continue Reading →
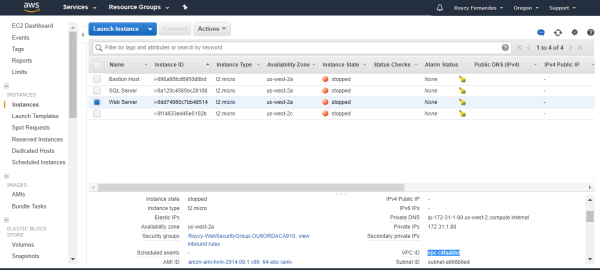
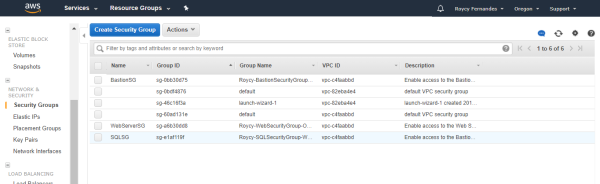
Basic Audit of AWS Environment – EC2
Security Configuration of Amazon Elastic Compute Cloud (EC2) Instances Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides resize-able computing capacity—literally, servers in Amazon's data centers—that you use to build and host your software systems By default, security groups allow all outbound traffic. You can't change the outbound rules for an EC2-Classic security... Continue Reading →
Basic Audit of AWS Environment – IAM
Auditing User Permissions in IAM An audit gives you an opportunity to remove unneeded IAM users, roles, groups, and policies, and to make sure that your users and software have only the permissions that are required. Periodically audit your security configuration to make sure it meets your current business needs. Use the IAM Policy Simulator to test... Continue Reading →